Security Architecture of AWS | Amazon Web Server

Working of AWS Architecture.
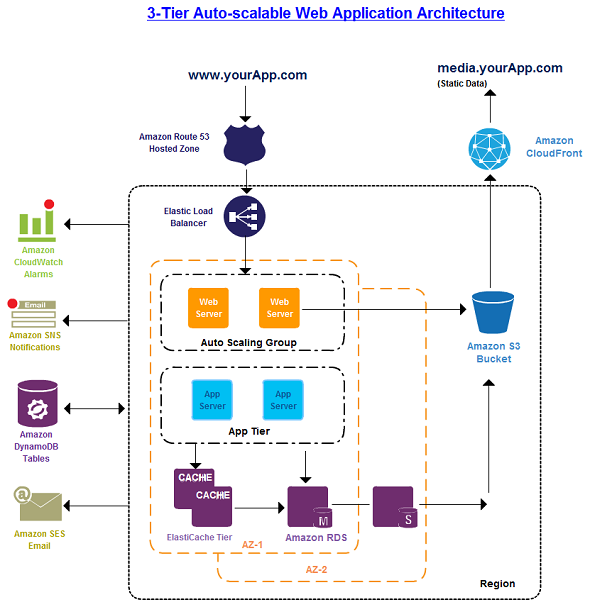
Content Delivery
Edge caching is still relevant in the Amazon Web Service cloud computing infrastructure. Any existing solutions in your web application infrastructure should work just fine in the AWS cloud. One additional option, however, is made available when using AWS, which is to utilize the Amazon CloudFront service1 for edge caching your website
Like other Amazon Web Services, there are no contracts or monthly commitments for using Amazon CloudFront – you pay only for as much or as little content as you actually deliver through the service.
Managing Public DNS
Moving a web application to the AWS cloud requires some DNS changes to take advantage of the multiple availability zones that AWS provides. To help you manage DNS routing, AWS provides Amazon Route 534 , a highly available and scalable DNS web service. Queries for your domain are automatically routed to the nearest DNS server and thus are answered with the best possible performance. Route 53 resolves requests for your domain name (for example, www.example.com) to your Elastic Load Balancer, as well as your zone apex record (example.com).
Host Security
Unlike a traditional web hosting model, inbound network traffic filtering should not be confined to the edge; it should also be applied at the host level. Amazon Elastic Compute Cloud (EC2) provides a feature called security groups. A security group is analogous to an inbound network firewall, for which you to specify the protocols, ports, and source IPs ranges that are allowed to reach your EC2 instances. Each EC2 instance can be assigned one or more security groups, each of which routes the appropriate traffic to each instance. Security groups can be configured so that only specific subnets or IP addresses have access to an EC2 instance, or they can reference other security groups to limit access to EC2 instances that are in specific groups.
For instance, in the example AWS web hosting architecture above, the security group for the web server cluster might allow access for any host only over TCP on ports 80 and 443 (HTTP and HTTPS) and from instances in the application server security group on port 22 (SSH) for direct host management. The security group of the application server cluster, on the other hand, might allow access from the Web Server security group for handling web requests and from your organization’s subnet over TCP on port 22 (SSH) for direct host management. In this model, shown above, your support engineers could log in directly to the application servers from the corporate network and then access the other clusters from the application server boxes. For a deeper discussion on security, go to the AWS Security Center5 . The center contains security bulletins, certification information, and security whitepapers that explain the security capabilities of AWS.
Load balancing across clusters of AWS Server.
Hardware load balancers are a common network appliance used in traditional web application architectures. AWS provides this capability through the Elastic Load Balancing6 service, a configurable load-balancing solution that supports health checks on hosts, distribution of traffic to EC2 instances across multiple availability zones, and dynamic addition and removal of Amazon EC2 hosts from the load-balancing rotation. Elastic Load Balancing can also dynamically grow and shrink the load-balancing capacity to adjust to traffic demands while providing a predictable entry point by using a persistent CNAME. The Elastic Load Balancing service also supports sticky sessions to address more advanced routing needs. If your application requires more advanced load-balancing capabilities you could run a software load-balancing.

Caching within the web application
In-memory application caches can reduce load on services and improve performance and scalability on the database tier by caching frequently used information. Amazon ElastiCache9 is a web service that makes it easy to deploy, operate, and scale an in-memory cache in the cloud. The in-memory cache that you create can be configured to automatically scale with load and to automatically replace failed nodes. Amazon ElastiCache is protocol-compliant with Memcached, which simplifies migration from your current on-premises solution.

Working of AWS Architecture.

Content Delivery
Edge caching is still relevant in the Amazon Web Service cloud computing infrastructure. Any existing solutions in your web application infrastructure should work just fine in the AWS cloud. One additional option, however, is made available when using AWS, which is to utilize the Amazon CloudFront service1 for edge caching your website
Like other Amazon Web Services, there are no contracts or monthly commitments for using Amazon CloudFront – you pay only for as much or as little content as you actually deliver through the service.
Managing Public DNS
Moving a web application to the AWS cloud requires some DNS changes to take advantage of the multiple availability zones that AWS provides. To help you manage DNS routing, AWS provides Amazon Route 534 , a highly available and scalable DNS web service. Queries for your domain are automatically routed to the nearest DNS server and thus are answered with the best possible performance. Route 53 resolves requests for your domain name (for example, www.example.com) to your Elastic Load Balancer, as well as your zone apex record (example.com).
Host Security
Unlike a traditional web hosting model, inbound network traffic filtering should not be confined to the edge; it should also be applied at the host level. Amazon Elastic Compute Cloud (EC2) provides a feature called security groups. A security group is analogous to an inbound network firewall, for which you to specify the protocols, ports, and source IPs ranges that are allowed to reach your EC2 instances. Each EC2 instance can be assigned one or more security groups, each of which routes the appropriate traffic to each instance. Security groups can be configured so that only specific subnets or IP addresses have access to an EC2 instance, or they can reference other security groups to limit access to EC2 instances that are in specific groups.
For instance, in the example AWS web hosting architecture above, the security group for the web server cluster might allow access for any host only over TCP on ports 80 and 443 (HTTP and HTTPS) and from instances in the application server security group on port 22 (SSH) for direct host management. The security group of the application server cluster, on the other hand, might allow access from the Web Server security group for handling web requests and from your organization’s subnet over TCP on port 22 (SSH) for direct host management. In this model, shown above, your support engineers could log in directly to the application servers from the corporate network and then access the other clusters from the application server boxes. For a deeper discussion on security, go to the AWS Security Center5 . The center contains security bulletins, certification information, and security whitepapers that explain the security capabilities of AWS.
Load balancing across clusters of AWS Server.
Hardware load balancers are a common network appliance used in traditional web application architectures. AWS provides this capability through the Elastic Load Balancing6 service, a configurable load-balancing solution that supports health checks on hosts, distribution of traffic to EC2 instances across multiple availability zones, and dynamic addition and removal of Amazon EC2 hosts from the load-balancing rotation. Elastic Load Balancing can also dynamically grow and shrink the load-balancing capacity to adjust to traffic demands while providing a predictable entry point by using a persistent CNAME. The Elastic Load Balancing service also supports sticky sessions to address more advanced routing needs. If your application requires more advanced load-balancing capabilities you could run a software load-balancing.

Caching within the web application
In-memory application caches can reduce load on services and improve performance and scalability on the database tier by caching frequently used information. Amazon ElastiCache9 is a web service that makes it easy to deploy, operate, and scale an in-memory cache in the cloud. The in-memory cache that you create can be configured to automatically scale with load and to automatically replace failed nodes. Amazon ElastiCache is protocol-compliant with Memcached, which simplifies migration from your current on-premises solution.
Dmca Ignored Hosting Provides you safe and secure cheap Offshore Hosting Best offshore hosting and Dmca Ignore hosting with 99.9% Up time Guarantee, with Ddos protection.
ReplyDelete