Web application security measures :
Firewalls
A firewall is a piece of software (or hardware) that controls what services are exposed to the
network. This means blocking or restricting access to every port except for those that should be
publicly available.
network. This means blocking or restricting access to every port except for those that should be
publicly available.
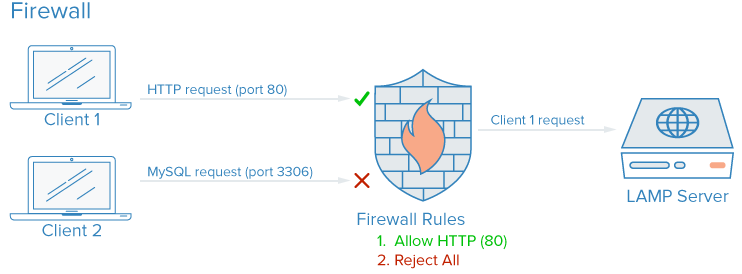
On a typical server, a number services may be running by default. These can be categorized into
the following groups:
the following groups:
- Public services that can be accesses by anyone on the internet, often anonymously. A good example of this is a web server that might allow access to your site.
- Private services that should only be accessed by a select group of authorized accounts or from certain locations. An example of this may be a database control panel.
- Internal services that should be accessible only from within the server itself, without exposing the service to the outside world. For example, this may be a database that only accepts local connections.
Firewalls can ensure that access to your software is restricted according to the categories
above. Public services can be left open and available to everyone and private services can be
restricted based on different criteria. Internal services can be made completely inaccessible to
the outside world. For ports that are not being used, access is blocked entirely in most
configurations.
above. Public services can be left open and available to everyone and private services can be
restricted based on different criteria. Internal services can be made completely inaccessible to
the outside world. For ports that are not being used, access is blocked entirely in most
configurations.
VPNs and Private Networking
Private networks are networks that are only available to certain servers or users. For instance, in DigitalOcean, private networking is available in some regions as a data-center wide network.
A VPN, or virtual private network, is a way to create secure connections between remote
computers and present the connection as if it were a local private network. This provides a
way to configure your services as if they were on a private network and connect remote
servers over secure connections.
computers and present the connection as if it were a local private network. This provides a
way to configure your services as if they were on a private network and connect remote
servers over secure connections.
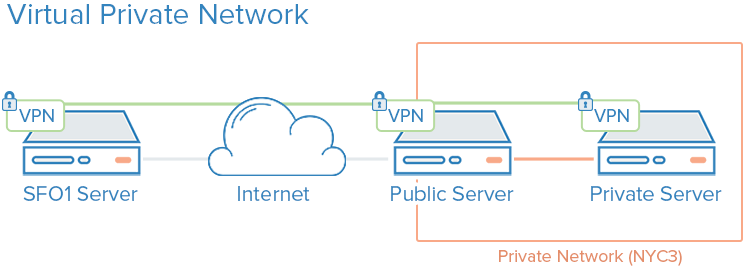
How Do They Enhance Security?
Utilizing private instead of public networking for internal communication is almost always
preferable given the choice between the two. However, since other users within the data
center are able to access the same network, you still must implement additional measures
to secure communication between your servers.
preferable given the choice between the two. However, since other users within the data
center are able to access the same network, you still must implement additional measures
to secure communication between your servers.
Public Key Infrastructure and SSL/TLS Encryption
Public key infrastructure, or PKI, refers to a system that is designed to create, manage, and
validate certificates for identifying individuals and encrypting communication. SSL or TLS
certificates can be used to authenticate different entities to one another. After authentication,
they can also be used to established encrypted communication.
validate certificates for identifying individuals and encrypting communication. SSL or TLS
certificates can be used to authenticate different entities to one another. After authentication,
they can also be used to established encrypted communication.
How Do They Enhance Security?
Establishing a certificate authority and managing certificates for your servers allows each
entity within your infrastructure to validate the other members identity and encrypt their traffic.
This can prevent man-in-the-middle attacks where an attacker imitates a server in your
infrastructure to intercept traffic.
entity within your infrastructure to validate the other members identity and encrypt their traffic.
This can prevent man-in-the-middle attacks where an attacker imitates a server in your
infrastructure to intercept traffic.
Each server can be configured to trust a centralized certificate authority. Afterwards, any
certificate that the authority signs can be implicitly trusted. If the applications and protocols
you are using to communicate support TLS/SSL encryption, this is a way of encrypting
your system without the overhead of a VPN tunnel (which also often uses SSL internally).
certificate that the authority signs can be implicitly trusted. If the applications and protocols
you are using to communicate support TLS/SSL encryption, this is a way of encrypting
your system without the overhead of a VPN tunnel (which also often uses SSL internally).
Service Auditing
Up until now, we have discussed some technology that you can implement to improve your
security. However, a big portion of security is analyzing your systems, understanding the
available attack surfaces, and locking down the components as best as you can.
security. However, a big portion of security is analyzing your systems, understanding the
available attack surfaces, and locking down the components as best as you can.

Service auditing is a process of discovering what services are running on the servers in your infrastructure. Often, the default operating system is configured to run certain services at boot.
Installing additional software can sometimes pull in dependencies that are also auto-started.
Service auditing is a way of knowing what services are running on your system, which ports they are using for communication, and what protocols are accepted. This information can help you configure your firewall settings.
How Does It Enhance Security?
Servers start many processes for internal purposes and to handle external clients. Each of these represents an expanded attack surface for malicious users. The more services that you have running, the greater chance there is of a vulnerability existing in your accessible software.
Once you have a good idea of what network services are running on your machine, you can begin to analyze these services. Some questions that you will want to ask yourself for each one are:
- Should this service be running?
- Is the service running on interfaces that it doesn't needs to? Should it be bound to a single IP?
- Are your firewall rules structured to allow legitimate traffic pass to this service?
- Are your firewall rules blocking traffic that is not legitimate?
- Do you have a method of receiving security alerts about vulnerabilities for each of these services?
This type of service audit should be standard practice when configuring any new server in your infrastructure.
How Difficult Is This to Implement?
Doing a basic service audit is incredibly simple. You can find out which services are listening to ports on each interface by using the
netstat command. A simple example that shows the program name, PID, and addresses being used for listening for TCP and UDP traffic is:sudo netstat -plunt
You will see output that looks like this:
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 887/sshd
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 919/nginx
tcp6 0 0 :::22 :::* LISTEN 887/sshd
tcp6 0 0 :::80 :::* LISTEN 919/nginx
The main columns you need to stay attention to are
Proto, Local Address, and PID/Program name. If the address is 0.0.0.0, then the service is accepting connections on all interfaces.Isolated Execution Environments
Isolating execution environments refers to any method in which individual components are run within their own dedicated space.

This can mean separating out your discrete application components to their own servers or may
refer to configuring your services to operate in
refer to configuring your services to operate in
chroot environments or containers. The level of isolation depends heavily on your application's requirements and the realities of your infrastructure.How Do They Enhance Security?
Isolating your processes into individual execution environments increases your ability to isolate any security problems that may arise. Similar to how bulkheads and compartments can help contain hull breaches in ships, separating your individual components can limit the access that an intruder has to other pieces of your infrastructure.
How Difficult Is This to Implement?
Depending on the type of containment you choose, isolating your applications can be relatively simple. By packaging your individual components in containers, you can quickly achieve some measure of isolation, but note that Docker does not consider its containerization a security feature.
Setting up a
Minimum-security guidelines that apply to all Web applications and that you should follow:chroot environment for each piece can provide some level of isolation as well, but this also is not foolproof method of isolation as there are often ways of breaking out of a chroot environment. Moving components to dedicated machines is the best level of isolation, and in many cases may be the easiest, but may cost more for the additional machines.Web application security measures
 Combination of the 4 following basic security measures in place:
Combination of the 4 following basic security measures in place:Security measure 1:
Ensure that each directory contains an index file by renaming the default page you want to be shown to index. Then make sure that all the internal links to that page are updated as well!
Security measure 2:
Create an empty index file. When arriving at the directory, a blank page will be shown, but you will no longer be displaying a directory listing. You could also provide a message and a clickable link on that page to take your visitors to the correct page.
Security measure 3:
Create an index file that contains a redirection to the page you want to be shown. There are many free and easily implemented code snippets available that will allow you to do so and your visitors will not even notice that they are being redirected.
Security measure 4:
If you have downloadable content that people have to pay for, do not keep it it the same directory as the sales page, but keep it in a separate, secure directory and set up your payment processor to that directory. This way you ensure that only people who have paid for the content have access to it.

When selling products online as an Internet Marketer or otherwise, you are more prone to people trying to get to your restricted content so as to avoid having to pay for it. These 4 basic security measures should help you drastically reduce the risk of unlawful access to your site and save you from a lot of headaches and worries.


Comments
Post a Comment